 The motivation for attacks on Critical National Infrastructure has typically swayed towards financial gain, but this is evolving with more emphasis being placed on hacktivism. The Energyst talks to Illumio’s Director of Critical Infrastructure Solutions Trevor Dearing about cybersecurity in the energy sector.
The motivation for attacks on Critical National Infrastructure has typically swayed towards financial gain, but this is evolving with more emphasis being placed on hacktivism. The Energyst talks to Illumio’s Director of Critical Infrastructure Solutions Trevor Dearing about cybersecurity in the energy sector.
With the current energy crisis and dated software, the sector is facing an increase in ransomware attacks. This was recently shown by the hacking of Tata Power in October due to decades old software. As a result of this increasingly dated security, there is a real need to adapt the ways in which attacks are managed, shifting from outright prevention to a policy of ‘assume breach’, coping with and limiting the impacts of inevitable attacks. “Energy security and energy supply is so vital that it becomes a prime target,” says Dearing.
Any cyberattack moves around so that it gets to the point in the system where it can have the highest impact. “This has been seen in the past through the unique example of hacking of a fish tank thermometer in a Las Vegas casino to steal intimate data, but mostly it’s through emails. For the last 35 years since cyber security has existed, companies have spent a lot of money trying to prevent those attacks. But they still happen. What we have to do is to reduce the impact of those attacks. What Illumio is about is containing attacks so if that if someone releases ransomware the attack couldn’t get to the finance centre or the grid in energy.”
These attacks will continue to grow as more devices become connected to the same networks. The outdated software on older hardware continues to open up more and more vulnerabilities. Recently there has been a shift the focus from prevention to surviving an attack. Infrastructure needs to be designed to be attack tolerant. “If a dodgy email is opened that’s bad, however, it’s our job is to stop it shutting down the entire grid,” comments Dearing.
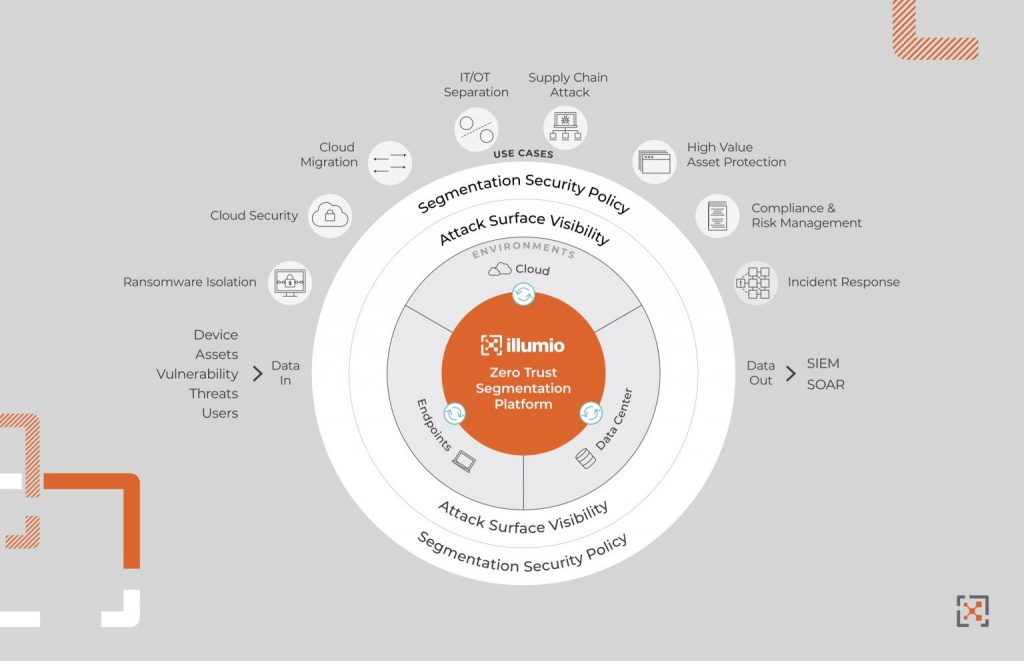
Zero Trust
There has been a move towards Zero Trust. Rather than having areas that are trusted and areas that are untrusted, the concept is that you should trust nothing. From there you only allow access through verified privilege. “Not working out what’s bad and keeping it out but work out what’s good and allow it in,” explains Dearing.
The challenge was that no one owned it or defined exactly what it was until NIST set out a clear definition. One thing to come out of this standardisation is the need to produce a map that shows all communication with all of your, the other is to be able to control that communication.
Everything is becoming smarter and relying on energy even things like phones with voice over internet. Dearing explains how the danger in increasing in the energy sector, “Many, many things are driving this in energy, obviously security and worrying about nation state players. But the energy crisis has also led to the desire to optimise things and this means data around supply and delivery management which requires intelligent equipment. Add to this new grid edge equipment such as storage batteries, solar panels, smart meters and so on and you are creating a new model but with multiple points of entry.”
Illumio creates a map and you can click on it and apply a rule to make Zero Trust relatively easy to manage. Any system will have vulnerabilities. The prime thing I have to do is to deliver electricity, for instance, everything is subservient to that. If someone does get into a network, you don’t want them getting to the relays and transformers. Illumio tests the system to see what would happen if we have a ransomware attack.
“The bad guy is getting more sophisticated,” says Dearing, “They’re getting better at avoiding a lot of the detection tools. If I attack a business down the road, I may get a little bit of money but if I can stop the electricity supply someone’s going to pay a huge amount to rectify it.” There’s a lot more analytics to work out, people want to know how much of their power is from renewables and so on, so there needs to be more smart technology on the grid. “As soon as you do that, it becomes more vulnerable. You just have to make sure that the development of IoT doesn’t outpace security. Regulators are worried about this. Many companies think the security guys are slowing us down, while the security guys will say the others are creating risk. Those teams need to be working together.”
There is a convergence of the IoT/OT (operational technology) security side and the IT security side. “There is a need to make sure that there is a single authority responsible for security across the whole organisation,” says Dearing, “Illumio can do both sides, OT & IT, we can show a map of that sever talking to that relay etc. Highlights new kit and doesn’t trust it until it is verified.” In fact, this disconnect could open organisations up to bigger security threats as hackers take advantage of the silo.
Illumio believes that organisations should prioritise a single and structured approach to their security defences to improve visibility and monitoring. Once this is in place, then they can look to take steps to enforce critical policies across their entire networks.



